
Unpacking & Reversing VIPKeyLogger
Introduction Lately, my malware analysis environment has been revolving door for data stealers, each one being very unique in its own way. But I encountered VIPKeyLogger, and it stood out from the...

Introduction Lately, my malware analysis environment has been revolving door for data stealers, each one being very unique in its own way. But I encountered VIPKeyLogger, and it stood out from the...
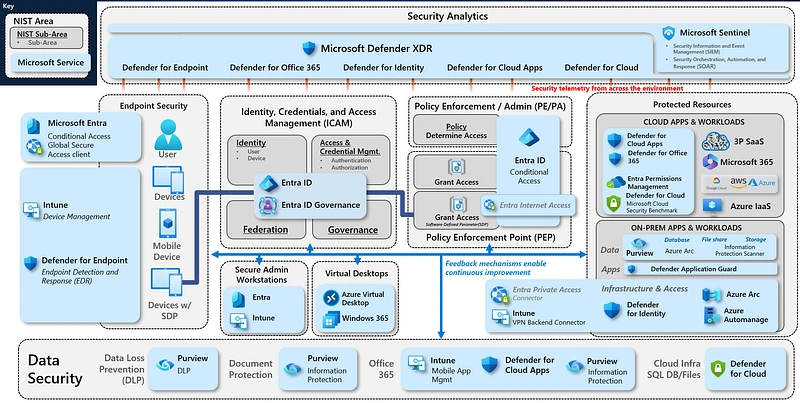
A few days ago, while scouring the never-ending vastness of the documentation, looking for some architectural references (outside of MCRA), I came to a page that blew my mind - Microsoft Learn Secu...
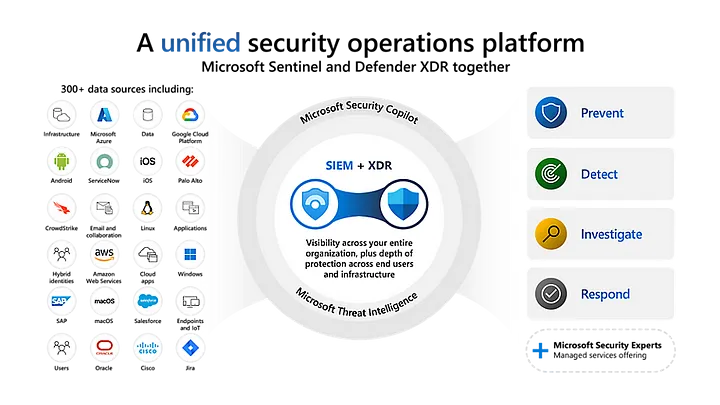
In a previous article, I discussed the Microsoft Defender XDR suite, its benefits, coverage, and different aspects. In this article, I will explain how you can have one pane of glass consisting of ...
Thanks Sometimes, I spend my time developing malware just for fun and have become really interested in process hollowing. Because of that, I decided to create this blog to share everything I’ve lea...
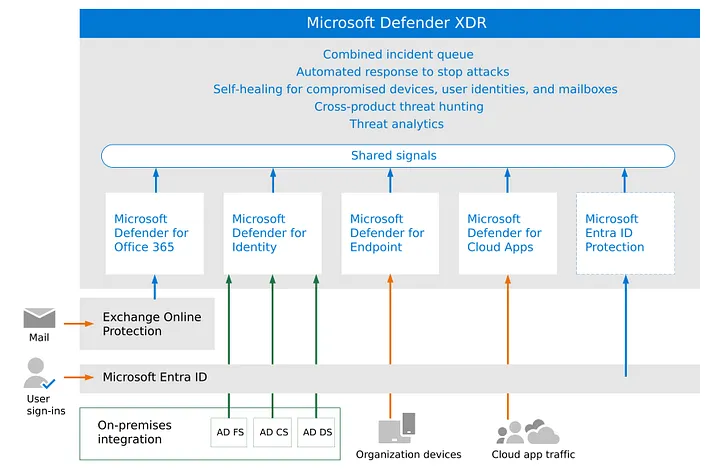
If you work in a corporation, there is always a question of security. Maybe your CISO sent an email with bullet points asking how different types of data and resources are protected from potential ...

As one of the leading IT certification providers, CompTIA offers intermediate certificates for anyone interested and starting in IT. Some of the most recognized CompTIA certificates include: Se...

This is part 3 and the last part of the exam guide for Azure Fundamentals. For the last topic, we will cover all the Tools for managing and deploying Azure resources along with Azure monitoring to...

If you’ve come this far I can already tell you went through my Part 1 of the exam guide for Azure Fundamentals. Going further on we will go through the following topics: Azure identity, a...

If you want to get into the Cloud (in this case, Azure Cloud specifically), this is your fundamental exam to get you started. Before diving any deeper here is a link to the AZ-900 Study guide and ...

I’m sure that you’ve had situations where you have asked yourself “OK, I have some certificates that we are using for SSL/TLS, also a few of the passwords and database connection strings, and encry...